Cyberthreats have scaled up.
Recent findings from the US Department of Homeland Security's Cyber Safety Review Board (CSRB) revealed a cyber attack on Microsoft by Storm-0558, a threat actor group. Additionally, Microsoft has faced persistent attacks from another group, Midnight Blizzard.
In response to this, Microsoft will be expanding its Secure Future Initiative, a program they launched last November, to protect themselves and their products from cyberattacks.
In a press release from Microsoft, they said, “We are making security our top priority at Microsoft, above all else—over all other features. We’re expanding the scope of SFI, integrating the recent recommendations from the CSRB as well as our learnings from Midnight Blizzard to ensure that our cybersecurity approach remains robust and adaptive to the evolving threat landscape.”
Microsoft said hiring decisions will have an important role in how they will be expanding SFI and “instill accountability” to the company’s senior leadership team and base their compensation on how well they perform. So, basically, they mean if Microsoft’s cybersecurity leaders do good in their jobs, they’re paid better.
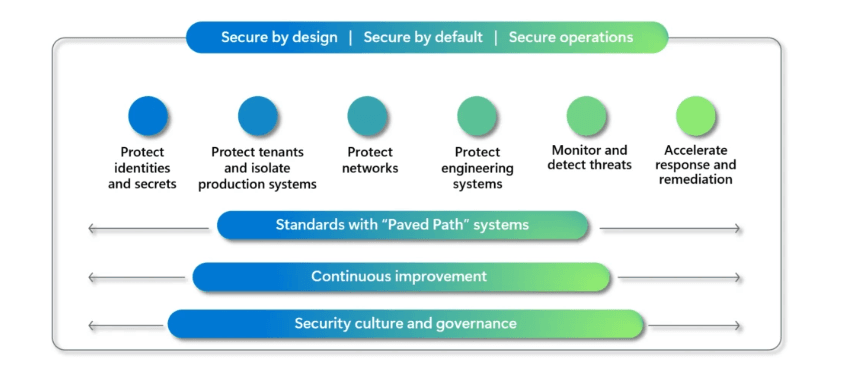
Microsoft said they changed their security approach, guided by three security principles:
- Secure by design: Security comes first when designing any product or service.
- Secure by default: Security protections are enabled and enforced by default, require no extra effort, and are not optional.
- Secure operations: Security controls and monitoring will continuously be improved to meet current and future threats.
This is followed by six security pillars:
1. Protect identities and secrets
Reduce the risk of unauthorized access by implementing and enforcing best-in-class standards across all identity and secrets infrastructure, and user and application authentication and authorization. As part of this, we are taking the following actions:
- Protect identity infrastructure signing and platform keys with rapid and automatic rotation with hardware storage and protection (for example, hardware security module (HSM) and confidential compute).
- Strengthen identity standards and drive their adoption through use of standard SDKs across 100% of applications.
- Ensure 100% of user accounts are protected with securely managed, phishing-resistant multifactor authentication.
- Ensure 100% of applications are protected with system-managed credentials (for example, Managed Identity and Managed Certificates).
- Ensure 100% of identity tokens are protected with stateful and durable validation.
- Adopt more fine-grained partitioning of identity signing keys and platform keys.
- Ensure identity and public key infrastructure (PKI) systems are ready for a post-quantum cryptography world.
2. Protect tenants and isolate production systems
Protect all Microsoft tenants and production environments using consistent, best-in-class security practices and strict isolation to minimize breadth of impact. As part of this, we are taking the following actions:
- Maintain the security posture and commercial relationships of tenants by removing all unused, aged, or legacy systems.
- Protect 100% of Microsoft, acquired, and employee-created tenants, commerce accounts, and tenant resources to the security best practice baselines.
- Manage 100% of Microsoft Entra ID applications to a high, consistent security bar.
- Eliminate 100% of identity lateral movement pivots between tenants, environments, and clouds.
- 100% of applications and users have continuous least-privilege access enforcement.
- Ensure only secure, managed, healthy devices will be granted access to Microsoft tenants.
3. Protect networks
Protect Microsoft production networks and implement network isolation of Microsoft and customer resources. As part of this, we are taking the following actions:
- Secure 100% of Microsoft production networks and systems connected to the networks by improving isolation, monitoring, inventory, and secure operations.
- Apply network isolation and microsegmentation to 100% of the Microsoft production environments, creating additional layers of defense against attackers.
- Enable customers to easily secure their networks and network isolate resources in the cloud.
4. Protect engineering systems
Protect software assets and continuously improve code security through governance of the software supply chain and engineering systems infrastructure. As part of this, we are taking the following actions:
- Build and maintain inventory for 100% of the software assets used to deploy and operate Microsoft products and services.
- 100% of access to source code and engineering systems infrastructure is secured through Zero Trust and least-privilege access policies.
- 100% of source code that deploys to Microsoft production environments is protected through security best practices.
- Secure development, build, test, and release environments with 100% standardized, governed pipelines and infrastructure isolation.
Secure the software supply chain to protect Microsoft production environments.
5. Monitor and detect threats
Comprehensive coverage and automatic detection of threats to Microsoft production infrastructure and services. As part of this, we are taking the following actions:
- Maintain a current inventory across 100% of Microsoft production infrastructure and services.
- Retain 100% of security logs for at least two years and make six months of appropriate logs available to customers.
- 100% of security logs are accessible from a central data lake to enable efficient and effective security investigation and threat hunting.
- Automatically detect and respond rapidly to anomalous access, behaviors, and configurations across 100% of Microsoft production infrastructure and services.
6. Accelerate response and remediation
Prevent exploitation of vulnerabilities discovered by external and internal entities, through comprehensive and timely remediation. As part of this, we are taking the following actions:
- Reduce the Time to Mitigate for high-severity cloud security vulnerabilities with accelerated response.
- Increase transparency of mitigated cloud vulnerabilities through the adoption and release of Common Weakness Enumeration (CWE), and Common Platform Enumeration (CPE) industry standards for released high severity Common Vulnerabilities and Exposures (CVE) affecting the cloud.
- Improve the accuracy, effectiveness, transparency, and velocity of public messaging and customer engagement.