Understanding the DOST hack: What really happened
A closer look at how the #opEDSA hackers broke in and what it means for our digital security
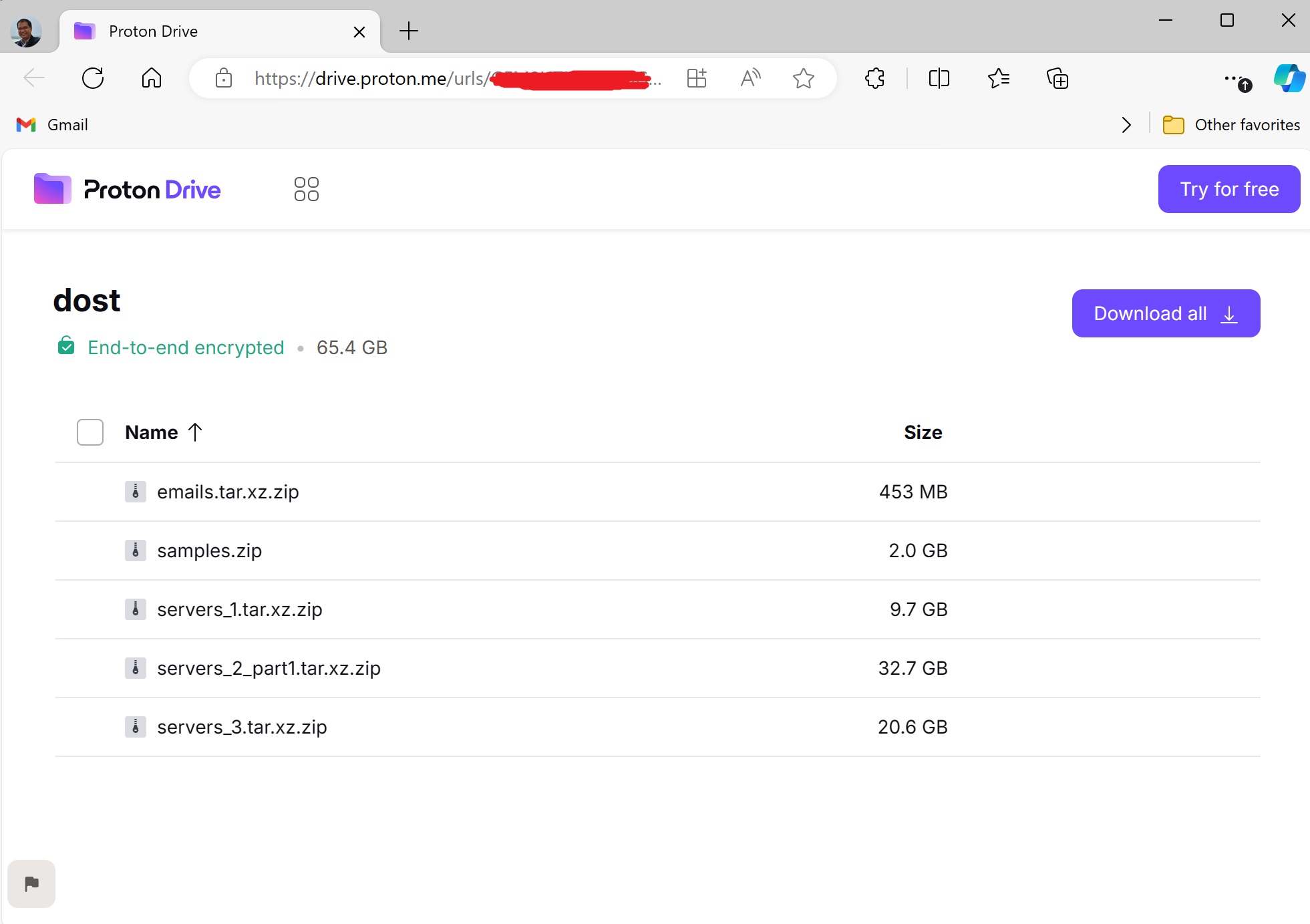
At A Glance
- The Department of Science and Technology (DOST) was specifically targeted in the cyberattack, indicating a deliberate effort to breach critical government infrastructure.
- The #opEDSA hackers employed a meticulous strategy, scanning DOST's servers and exploiting vulnerabilities step by step to gain deeper access.
- Critical weaknesses within DOST's digital infrastructure were exposed, including sensitive data like database credentials and vulnerabilities allowing arbitrary code execution.
- Domain controllers and network-attached storage (NAS) devices were among the compromised systems, highlighting the extent of the breach and potential data exposure.
- The incident shows the urgent need for enhanced cybersecurity measures within government organizations to safeguard against evolving cyber threats and protect critical digital assets.
In a meticulously orchestrated cyber attack that sent shockwaves through the Philippine government, a hacktivist group known as #opEDSA successfully breached the Department of Science and Technology (DOST). The attackers, methodical in their approach, exposed critical vulnerabilities within the department's digital infrastructure, leaving a trail of compromised systems and exposed vulnerabilities and raising serious concerns about the nation's cybersecurity posture.
The #opEDSA hackers meticulously planned and executed their attack. The group described how their digital siege progressed in a post on their website.
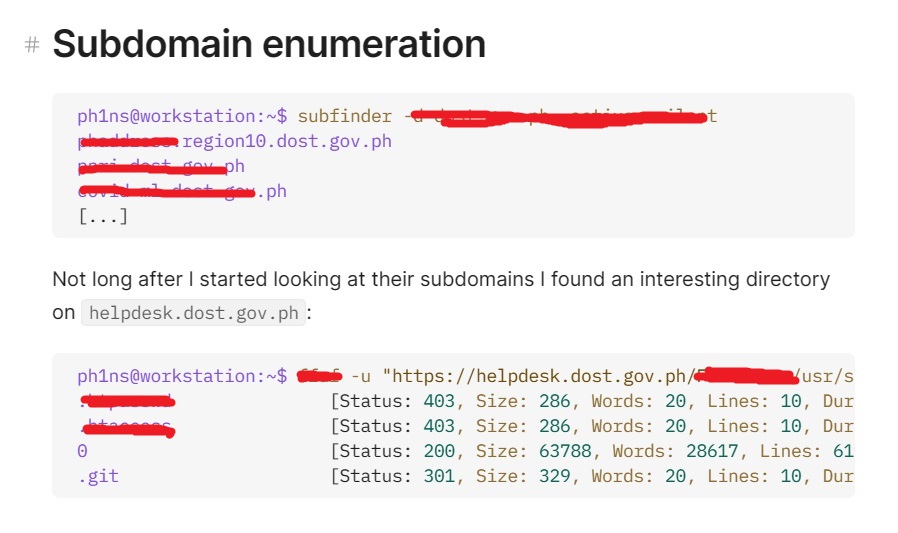
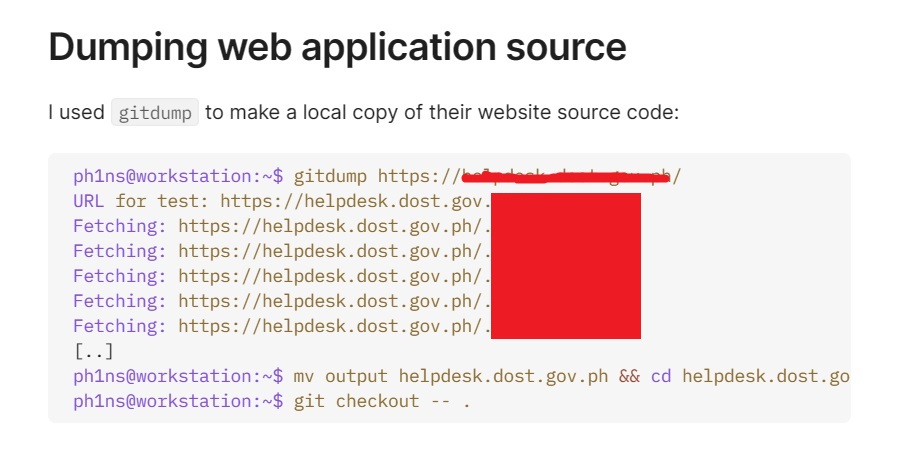
1. Initial Reconnaissance: The group initiated their mission by scanning DOST's subdomains. Their keen eye quickly detected an exposed `.git` directory on the `helpdesk.dost.gov.ph` server. Using tools like `ffuf` and `gitdump,` the hacker cloned the website's source code, unearthing sensitive information such as database credentials.
2. Dangerous Discoveries: The hacker stumbled upon an interesting PHP `eval` function within the source code. This vulnerability allowed arbitrary code execution, potentially compromising critical systems. The hacker's persistence paid off as they identified a network of interconnected domains hosted on the same server. Each domain harbored its own set of vulnerabilities.
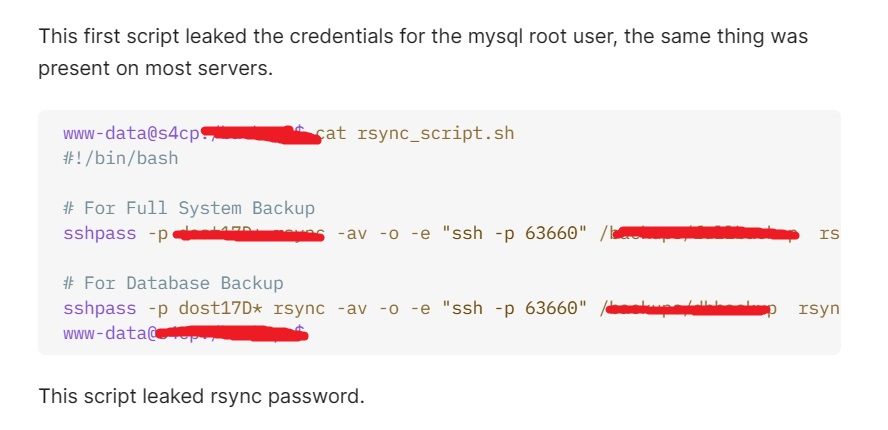
3. Database Credentials and More: Scripts found in a `/backups/` directory across multiple servers leaked MySQL root user credentials, providing deeper access to DOST's infrastructure. The hacker's journey led them to NAS (Network-Attached Storage) devices associated with the DOST. These devices contained a staggering 25 terabytes of data, including outdated network diagrams and other sensitive files.
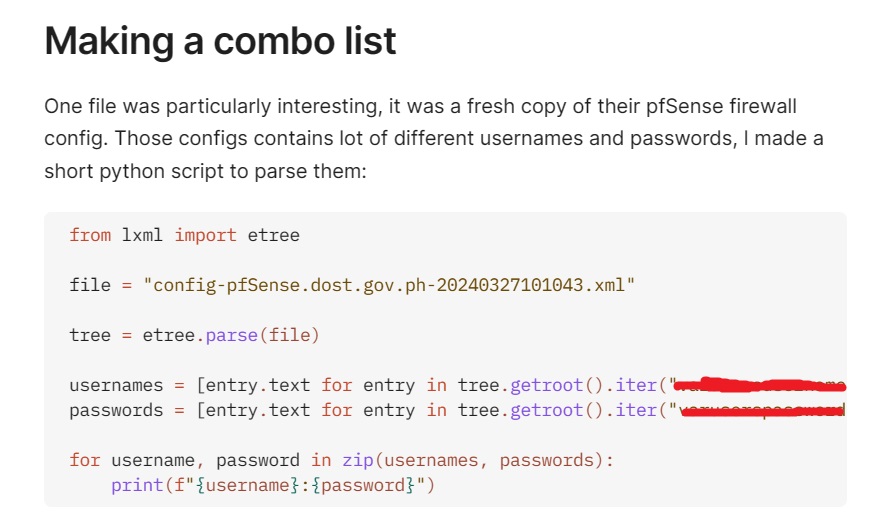
4. The Firewall and Domain Controller: Parsing a pfSense firewall configuration file using a Python script, the hacker extracted numerous usernames and passwords. Armed with this information, the hacker executed a password-spraying attack on the Domain Controller. Their persistence paid off, granting them coveted Domain Administrator access.
5. Lessons Learned: The DOST hack serves as a reminder of the critical importance of sound cybersecurity practices. Organizations must remain vigilant, patch vulnerabilities promptly, and implement stringent access controls to prevent unauthorized entry.
The DOST hack highlights the increasing sophistication of cyber threats and the urgent need for strong cybersecurity measures within government organizations. It reminds us that no entity is immune to cyberattacks. The incident prompted calls for thorough investigations, vulnerability identification, and a comprehensive cybersecurity strategy to protect the Philippines' critical digital assets.
The motivations of the hacktivist group #opEDSA linger in the shadows. Their actions suggest a desire to expose government weaknesses and potentially raise awareness about social or political issues. Whether their methods are justified remains hotly debated, but their act has undeniably brought national cybersecurity into sharp focus.
(At first, the hacker group was thought to be called ph1ns. It turns out that ph1ns (pronounced as fins) is a member of an unnamed group of hackers. According to ph1ns, the group would like to be known as #opEDSA.)