The following is fiction that is loosely based on several TRUE incidents that happened at BNSHosting.net
The air in the boardroom at ABC Corp hung heavy with tension as the CEO, Richard Daniels, pounded his fist on the polished mahogany table. “I’ve had enough of this!” he bellowed. “My emails aren’t reaching anyone! Fix it!” A million dollar project bid hung in the wind as a result of this email issue.
Thus began a cascade of events that would expose a sinister web of cyber intrigue, centered in the Philippines, where the internet struggled against the constraints of poverty, lax security awareness, and a corporate landscape with IT departments drowning in a sea of neglect.
The beleaguered IT Manager, Julia Mendoza, knew she had a storm on her hands. She quickly coordinated with BNSHosting.net, their mail server hosting provider. A quick check showed that the mail server was blacklisted!


courtesy of MXTOOLBOX.com
The MX server for ABC Corp was tainted. They were blacklisted by renowned providers. A roll call of ominous listings unveiled the extent of the problem. The blacklisting wasn’t a random act; it was a targeted hit.
As the investigation unfolded, they discovered a shadow lurking in the digital realms. Diving into the labyrinth of logs, BNSHosting.net unearthed a compromised user email account. This account was logged in from users outside of the Philippines. It was used to send out thousands of spam emails.
The breadcrumbs led them to a series of ominous entries — a relentless storm of brute force SASL authentication failures. A compromised user: [email protected].
Dec 28 09:49:01 mailserver03.-bnshosting-net dovecot: imap-login: Login: user=<[email protected]>, method=PLAIN, rip=171.233.176.xx, lip=202.91.16y.xx, mpid=64402, TLS, session=
Dec 28 09:50:02 mailserver03.-bnshosting-net dovecot: imap-login: Login: user=<[email protected]>, method=PLAIN, rip=71.40.52.xx, lip=202.91.16y.xx, mpid=64877, TLS, session=
Dec 28 09:53:14 mailserver03.-bnshosting-net dovecot: imap-login: Login: user=<[email protected]>, method=PLAIN, rip=38.207.136.xx, lip=202.91.16y.xx, mpid=66425, TLS, session=<7IbCLYgNroMmz4g1>
The logs whispered the tale of attempted intrusion. it was only a matter of time before the hackers correctly guessed the (simple) passwords. Eventually the hackers compromised the user account. It was the gateway to the network, and the hackers, driven by coordinated precision, had seized the throne. But who were they?
Coordinating with PHCert and the DICT’s Cybercrime Division, the malevolent shadows were revealed to belong to a hacker named “BlackRock.”
The tendrils of his digital influence stretched across the archipelago, a menace that transcended mere geographical borders. At this point, the priority was to stop all the spams that were still awaiting delivery in the mail queues. BNSHosting.net asked for permission to delete all of these.
The compromised account was quickly disabled first. Then its passwords were changed to more complex ones that had to be easy to remember and use. In addition, considering the relentless attacks on ABC Corp’s email accounts, BNSHosting.net, proposed additional measure: implement two-factor authentication.
Julia liked the idea. This meant that even if hackers were able to somehow guess or obtain the actual credentials of their users, it still needed a PIN code that was generated on the users’ phones. Access would be denied until the hacker could get all three items: Username, Password and PIN code.
Julia had informed Richard that several steps were needed to be done by ABC corp. Julia needed to make sure that the breach was limited to the emails and not expanded to the corporate network. The fear was that most users had the SAME credentials for both their email accounts and ACCESS to the corporate network. The damage could be worse had the hackers done what we call “Lateral expansion”.
The hackers could use the hacked email credentials to gain entry into the corporate network. Once inside the hackers could extract corporate data and encrypted them. Ransomware usually follows.
She followed this handy checklist that can be found in this site: Public Incident Response Ressources / Public Playbooks · GitLab. A sample playbook for Account compromised is reproduced below:
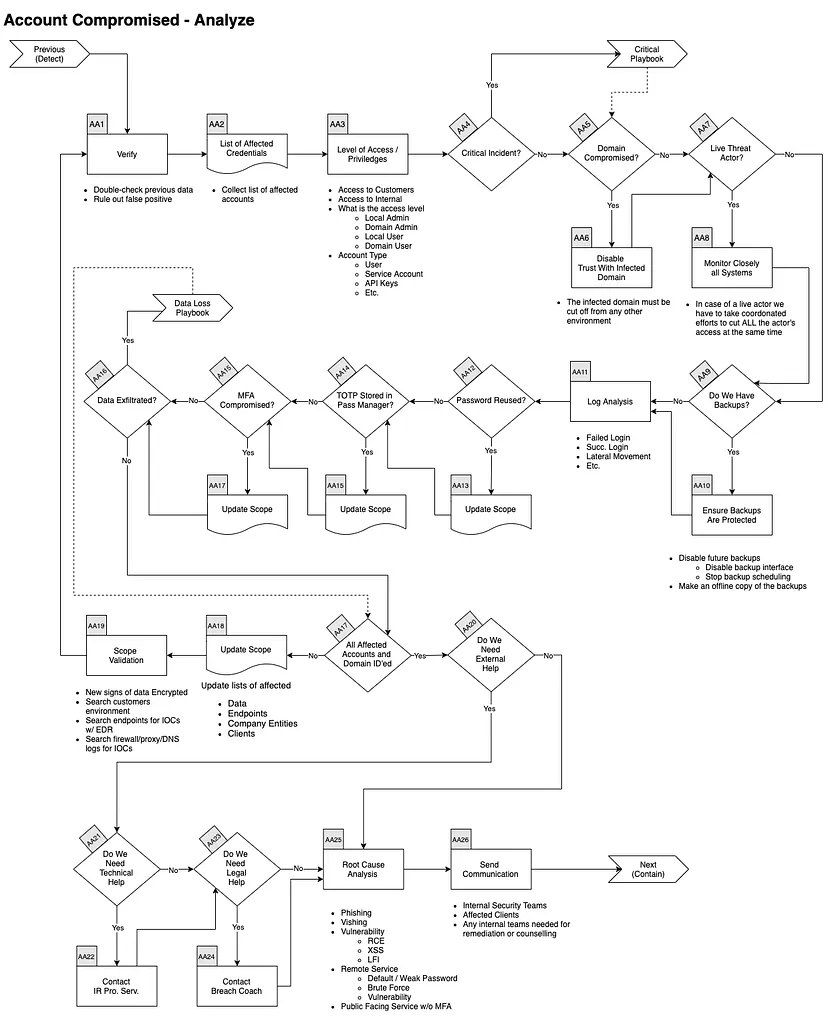

Public Incident Response Ressources / Public Playbooks · GitLab
Thankfully, the logs showed no evidence of lateral expansion. But as defense against future outbreaks, the lessons learned from each breach can serve as a powerful method of hardening the security of each network. These additional barricades can be used to raise the bar against the unseen shadows lurking in the cyber alleys.
As the sun dipped below the horizon, casting long shadows over Manila, the battle between security and intrusion continued, unseen and relentless.
PostScript:
In the aftermath of the email breach incident, Richard, having personally witnessed the malicious consequences of security lapses, is NOW committed to bolstering investments and allocating additional resources to enhance the network’s security.
He has gained a profound understanding of how neglecting fundamental security best practices poses a serious threat to what accountants refer to as the assumption of “Going Concern,” potentially jeopardizing the entire company’s operations.
“Your voice matters!”
Join the conversation and enrich our narrative with your unique insights. Share your thoughts, experiences, and perspectives to make this story a collaborative masterpiece. Together, we can make this story truly extraordinary. Join in and let your words become a part of the adventure!