Major data breach at Agricultural Credit Policy Council (ACPC) exposes sensitive information
Hacker exploits vulnerabilities in ACPC's systems, raising alarms anew about government cybersecurity practices
At A Glance
- DOST and PNP hacker, ph1ns, exploited a vulnerability in the ACPC's website to obtain a git token and access the agency's code repository.
- Over 37 GB of data, including personally identifiable information and login credentials, were exposed.
- ph1ns discovered database credentials within the repository, granting access to sensitive information such as usernames and passwords.
- The breach highlighted significant security weaknesses, including exposed sensitive information, weak security practices (like plaintext passwords), and inadequate validation checks.
- The incident raises serious concerns about the cybersecurity procedures of government agencies and underscores the importance of robust security measures for protecting sensitive information.
The Agricultural Credit Policy Council (ACPC) has been hacked, exposing sensitive data and raising concerns about government agency security. Ph1ns, a hacker who gained unauthorized access to the ACPC's internal systems, revealed the breach. The hacker was also responsible for several hack attacks on government agencies, including the DOST and the PNP.
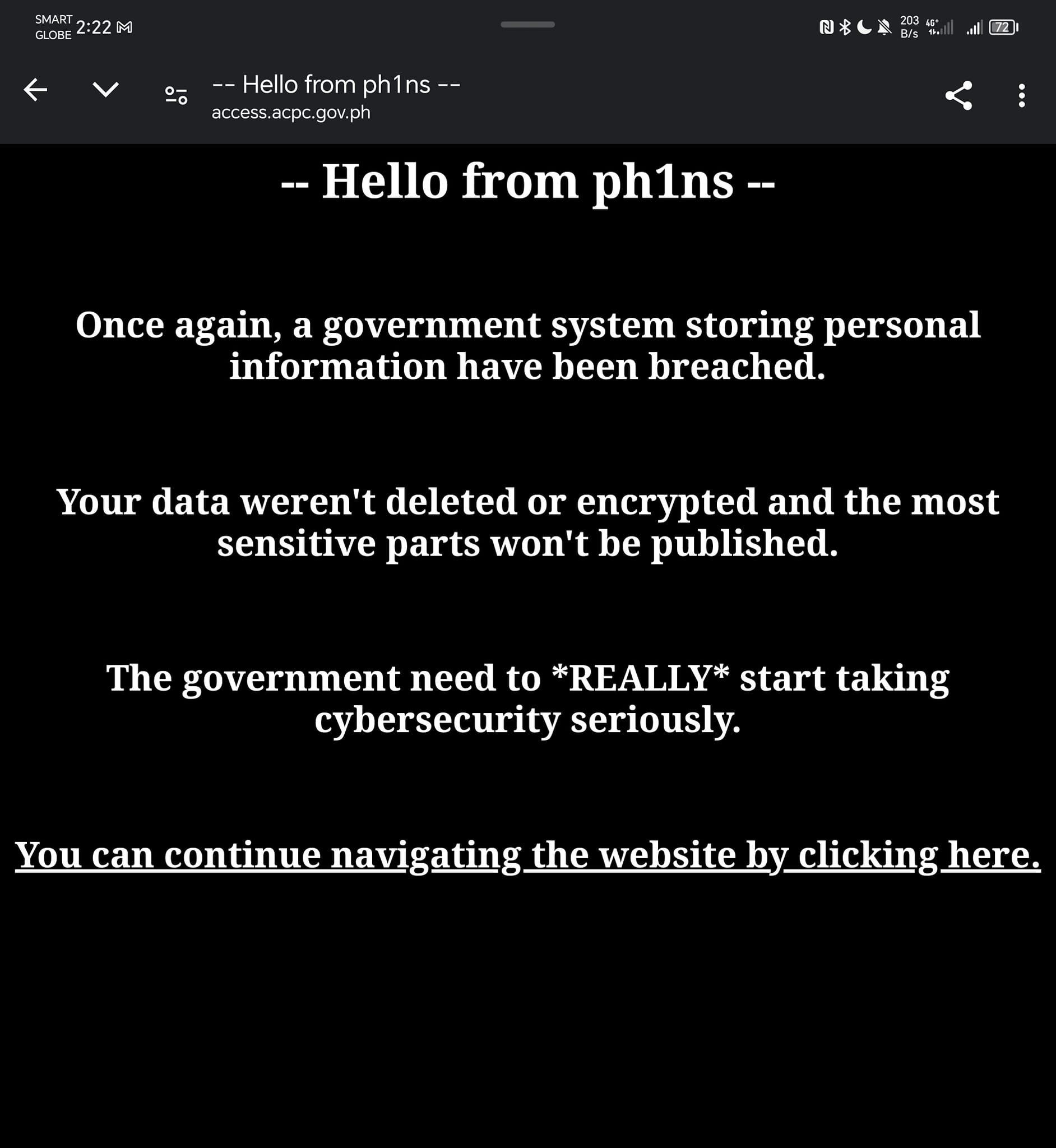
Ph1ns claims to have exploited a vulnerability in the ACPC's website, allowing him to obtain a git token and access the agency's code repository. The hacker said he discovered database credentials within the repository, granting him access to sensitive information, including usernames and passwords. Ph1ns claimed that more than 37 Gigabytes of data, including personally identifiable information and login credentials, were exposed because of the breach. In a post on BreachForums, a hacking forum where hackers and cybercriminals share data and information, Ph1ns announced the breach.
The hacker bypassed the ACPC's file upload restrictions, allowing him to execute commands on the agency's servers. Although the extent of the damage is still unknown, the incident raises serious concerns about the ACPC's cybersecurity procedures and the potential misuse of the compromised data.
The ACPC has not yet released an official statement regarding the incident. This breach again reminds us of the importance of solid cybersecurity measures for government agencies, especially those dealing with sensitive information.
According to the hacker, the breach on the ACPC website involved several steps, each exploiting different vulnerabilities. Here's a detailed breakdown of the process:
1. Discovery of exposed `.git` directory
Initially, the attacker discovered that the `.git` directory was exposed on the ACPC's website. Although unavailable, bots had cached the page, revealing a Git token.
2. Exposed Git token
The cached page exposed a valid Git token, which provided full access to the repository. The token was embedded in the repository configuration.
3. Cloning the repository
Using the exposed Git token, the attacker cloned the repository.
4. Searching for sensitive information
Once the repository was cloned, the attacker searched for sensitive information. They found database credentials in a file named `learn.php`:
5. Finding a script for database access
The attacker found a script called `phprunner.php` on the server, which allowed connecting to the database using the discovered credentials.
6. Exploiting the script
By analyzing the source code of `phprunner.php,` the attacker figured out how to execute custom SQL queries:
7. Dumping user data
Using the custom query execution feature, the attacker dumped the list of usernames and passwords. They discovered that the passwords were stored in plaintext.
8. Accessing user accounts
With plaintext passwords, the attacker can log into any user account on the web application. They chose a non-admin account and initiated a loan request to upload documents.
9. Bypassing file extension restriction: The upload functionality had weak file extension validation, which could be bypassed using double extensions like `file.png.php.`
10. Uploading a webshell
The attacker uploaded a web shell named `cmd.png.php` using the document upload feature. The web shell's name included a timestamp and email, making it tricky to retrieve.
11. Executing commands
By accessing the list of loan requests as an admin, the attacker found their uploaded webshell and used it to execute commands on the server.
The hack was successful due to a combination of exposed sensitive information, weak security practices (like plaintext passwords), and inadequate validation checks. The attacker leveraged these vulnerabilities to gain unauthorized access to the repository, database, and, eventually, the web server.