Hacker breaches PNP online systems anew
Leaked information include data of the Chief PNP, the spokesperson, and government officials
At A Glance
- The hacker ph1ns infiltrated the Philippines National Police (PNP) systems, compromising over 393,894 rows of personal information from the "PNP Logistics Data Information and Management System" (PLDIMS).
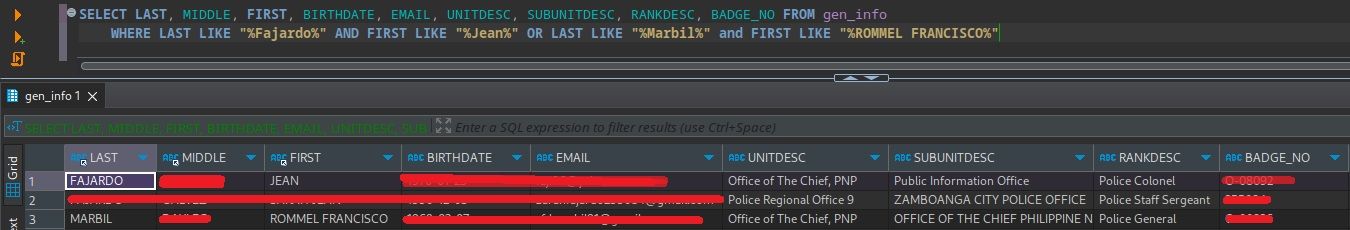
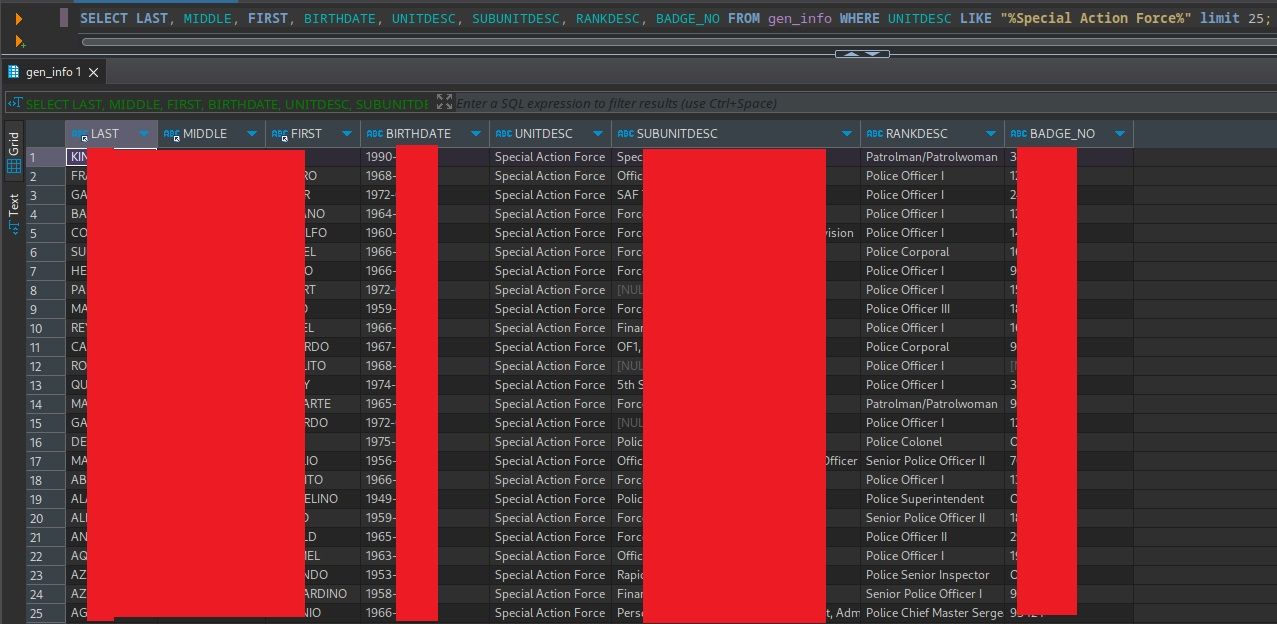
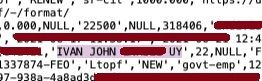
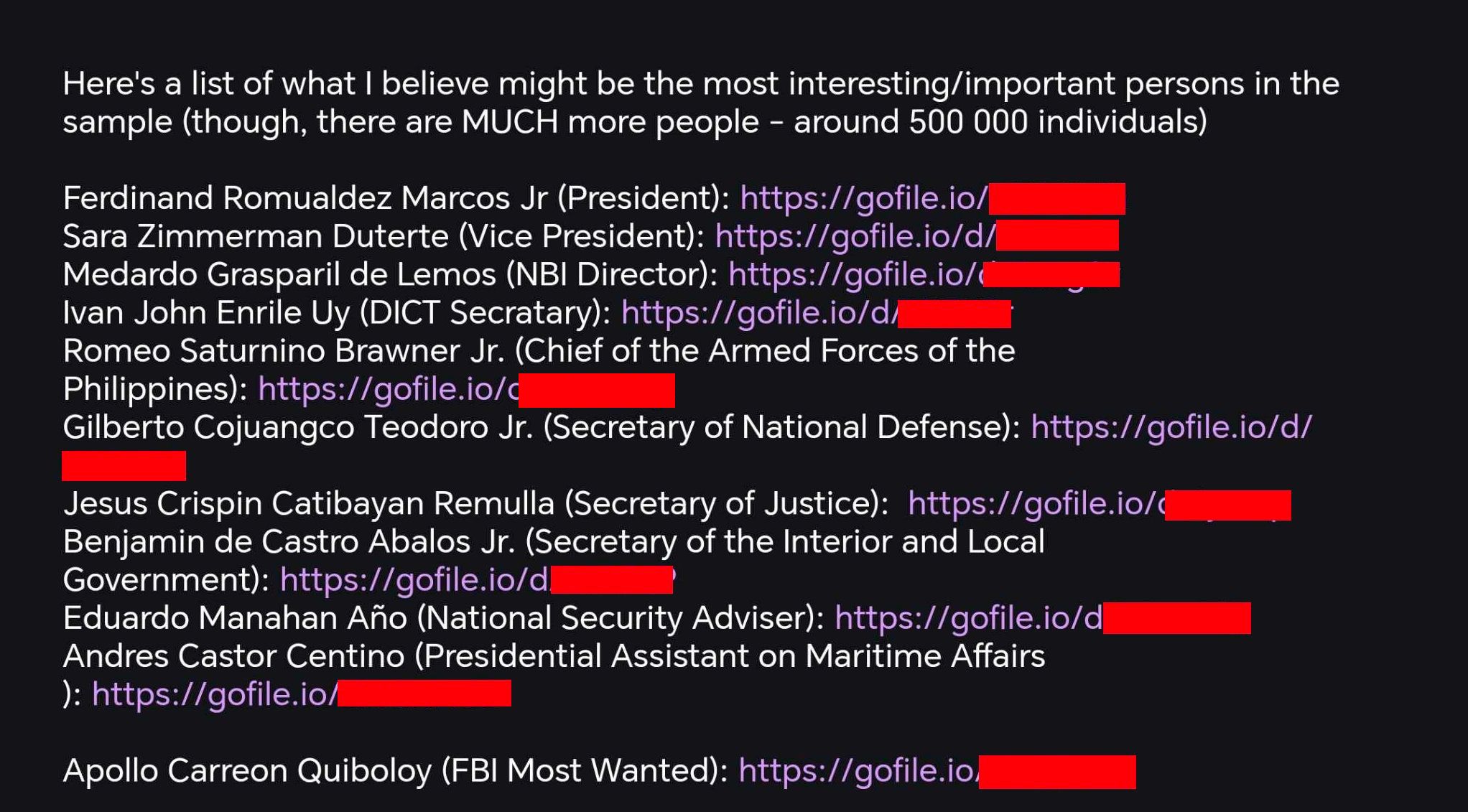
- After few days, the hacker breached another PNP system, the Firearms and Explosive office. This time, the leaked data includes names, birthdates, unit assignments, email addresses, and detailed personal information of Special Action Forces personnel and high-ranking officials, including the Chief PNP, the spokesperson, and DICT Secretary Ivan Uy.
- The breach began with ph1ns exploiting a vulnerable server and bypassing email verification on the PNP's Firearms and Explosives Office (FEO) Online License/Permits Application platform.
- Ph1ns leveraged a Local File Inclusion (LFI) vulnerability and other flaws to access and download sensitive files, including the <strong>.env</strong> file containing critical environment variables, resulting in the theft of approximately 1.6 terabytes of data.
- Ph1ns suggested several measures to prevent future breaches, including deploying Web Application Firewalls (WAF), patching vulnerabilities, using Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS), implementing whitelisting, and monitoring all connections to sensitive services.
In a daring cyber attack reminiscent of its previous exploits, an elusive hacker, known as ph1ns, has once again infiltrated the Philippines National Police (PNP) systems.
Just recently, ph1ns, who previously breached the Department of Science and Technology (DOST) and deleted 25 terra bytes of data from the agency's system, also gained access to the "PNP Logistics Data Information and Management System (PLDIMS)", disrupting the platform, and rendering it inaccessible. ph1ns shared the link to the evidence of the breach, including a database sample containing over 393,894 rows of personal information, such as names, birthdates, unit assignments, and email addresses. The hacker attributed the breach to a series of human errors.
ph1ns continued his attack on the PNP systems, this time the focus was on the Firearms and Explosives Office (FEO) databases.
The breach began when ph1ns stumbled upon a vulnerable server: `https://103.152.214.xxx/`, which turned out to be the PNP's FEO Online License/Permits Application platform. The hacker's initial attempt to create an account at `/register` resulted in an unexpected error—an oversight that would prove costly for the PNP.
Undeterred, ph1ns leveraged the error message to gain access. By fabricating an email address (`[email protected]`), the hacker bypassed email verification and successfully created an account. But this was just the beginning.
The hacker's next discovery was a vulnerable endpoint: `/references/downloadfile`. This flaw allowed ph1ns to download files from the server. By exploiting a Local File Inclusion (LFI) vulnerability, ph1ns could traverse directories and access sensitive information.
Ph1ns didn't stop there. The hacker identified two methods to access the `.env` file containing critical environment variables: first, analyzing the leaked web application's full path revealed during debugging; and second, fetching the file via the `/proc/self/CWD/` directory in the server's filesystem.
In an email released after the breach, ph1ns attributed the successful infiltration to human error within the PNP's security protocols. This serves as a reminder that even the most secure systems can be compromised when users inadvertently create vulnerabilities. Indeed, ph1ns said, the user remains the weakest link in any security posture.
The consequences were severe. Ph1ns gained access to terabytes of data from the FEO databases, and the PNP suffered a staggering loss of approximately 1.6 terabytes of sensitive information. The hacker claims that the data he downloaded includes names, addresses, birthdays, civil status, emails, TIN numbers, mobile numbers, telephone numbers, details of next of kin, the date and expiry of the neuro test, and the date, expiration, and result of the drug test. He also claimed that there are more than 500,000 names in the list that he downloaded.
DICT Undersecretary for Infostructure Management, Cybersecurity and Upskilling Jeffrey Ian C. Dy informed the Manila Bulletin that the DICT has met with NBI, PNP, NSC on Monday, May 20, and these agencies were already looking into the incident. "We will approach this collectively with the law enforcement and intelligence agencies. We already are ID-ing the cybercriminal PH1NS and we are confident we’ll be able to find PH1NS and his collaborators. We already found how he entered the system and laterally moved from one system in PNP, to another. We also have his TTPs." Usec Dy said.
Dy added that there is an ongoing crackdown on cyber criminals internationally. "Breachforums has been taken over by the FBI. Meta and Youtube are cracking down on hacking collectives attacking government and civilian computer systems. We are also coordinating with our international partners to divulge information they gathered from these takedowns to apprehend local cyber criminals," said Dy.
The PNP-FEO breach highlights the critical need for organizations to strengthen their cybersecurity defenses. As ph1ns continues to exploit vulnerabilities, the PNP must take immediate action to secure its systems, protect citizens' data, and hold those responsible accountable for their actions.