At A Glance
- The hacking group Ph1ns claims responsibility for a significant cyber attack on the Department of Science and Technology (DOST) servers, gaining access to critical infrastructure and encrypting the Domain Controller, effectively locking out authorized users.
- According to sources at the Department of Information and Communications Technology (DICT), the hackers deleted 25 Terabytes of data, causing widespread disruption beyond mere information loss.
- Ph1ns left a message on one of the compromised servers, criticizing political dynasties and oligarchic control in the Philippines. The manifesto rejects political indebtedness and calls for an end to favoritism towards the wealthy elite.
- The message from Ph1ns is signed with #opEDSA, referencing the historic People Power Revolution of 1986 in the Philippines, inviting others to join their cause against corruption and inequality.
- Ph1ns provides an email address, [email protected], encouraging individuals sympathetic to their cause to join their ranks in what they describe as a digital crusade, highlighting the growing trend of politically motivated hacking and the role of hacktivism in modern society.
The cyber landscape is once again ablaze with controversy as a hacking group known as Ph1ns claims to have launched a devastating attack on the Department of Science and Technology (DOST) servers. The group asserts that it has gained access to critical infrastructure, including hypervisors, Network-Attached Storage (NAS), and routers, and even obtained Domain Administrator privileges, allowing it unrestricted access to employee computers. Adding insult to injury, it boasts about encrypting the Domain Controller, effectively locking out authorized users.
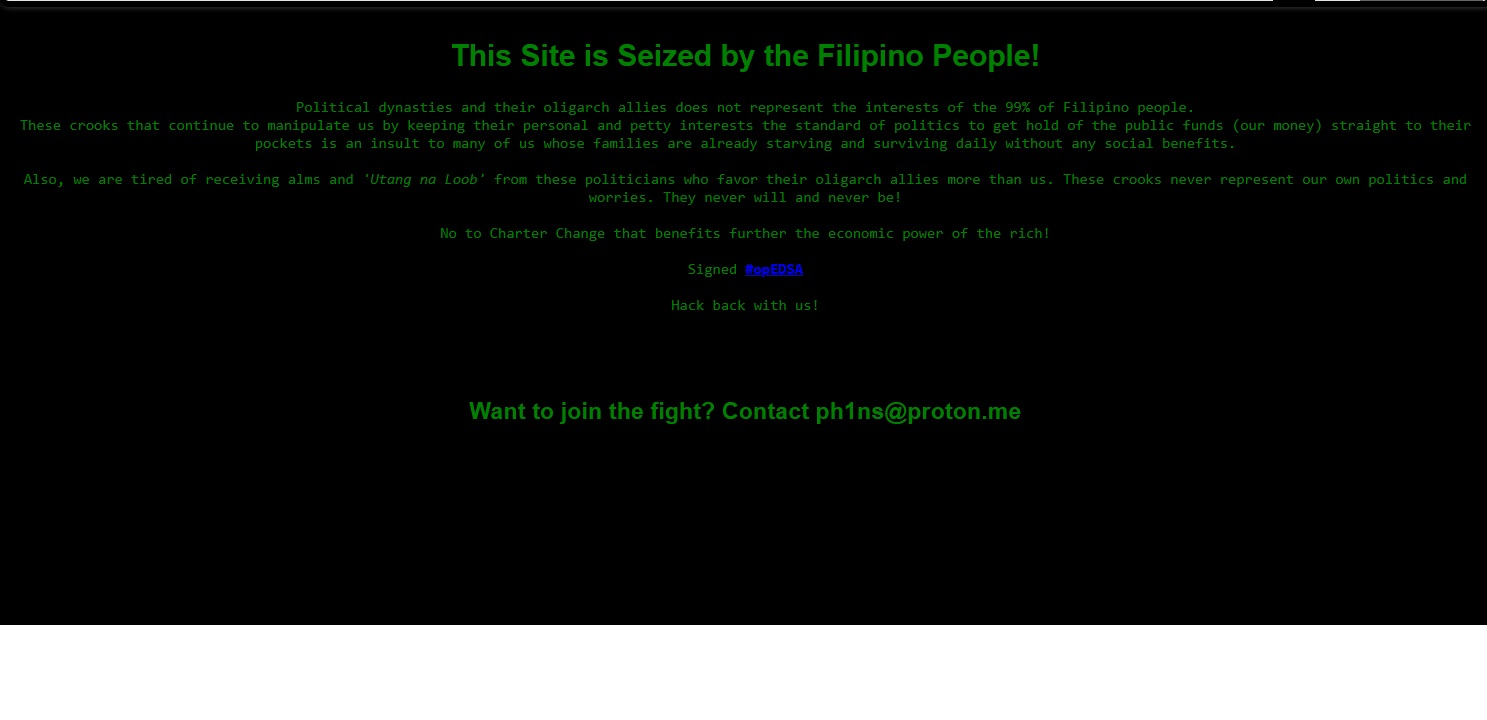
According to our sources at the Department of Information and Communications Technology (DICT), the hackers have wrought havoc by deleting 25 Terabytes of data. However, their intrusion has an impact beyond mere data deletion. On one of the compromised servers, Ph1ns left behind a message that reads: "This Site is Seized by the Filipino People!"
The message left by Ph1ns delves into the socio-political realm, decrying the influence of political dynasties and their oligarch allies who allegedly fail to represent the interests of the majority. The hackers accuse these elites of manipulating the political landscape to serve their agendas while ordinary Filipino families struggle to survive without adequate support.
The manifesto unequivocally rejects the notion of indebtedness ("Utang na Loob") to politicians and calls for an end to the cycle of favoritism towards oligarchs. It vehemently opposes any changes to the constitution that would further concentrate economic power in the hands of the wealthy.
Signed off with #opEDSA, a nod to the historic People Power Revolution of 1986, the message from Ph1ns invites others to join their cause and 'hack back' against what they perceive as entrenched corruption and inequality. This call to action raises important questions about the role of hacktivism in modern society and the potential for cyber attacks to be used as tools of dissent and activism.
In a bold move, Ph1ns provides an email address, ph1ns @ proton.me, encouraging individuals sympathetic to their cause to reach out and join their ranks in this digital crusade.
The infiltration of DOST servers by Ph1ns reminds us of the vulnerability of even obviously secure systems in the face of determined cyber adversaries. It also shows the growing trend of politically motivated hacking, where cyberattacks are wielded as tools of dissent and activism in addition to their traditional motives of espionage and financial gain. As authorities scramble to contain the fallout and bolster cybersecurity measures, the debate over the ethics and efficacy of hacktivism rages on.
UPDATE: DICT Undersecretary for Infostructure Management, Cybersecurity and Upskilling Jeffrey Ian C. Dy stated, "Our alarms detected the attack on DOST around 10PM and we recognize the need to improve the automated response mechanisms of our NSOC. We are currently engaged with DOST to bring back their services ASAP, and to improve our detection and incident response capability. We also already alerted our contacts in the NBI, and the security establishment about a local group who has claimed responsibility for the attack."