Cybersecurity case: How DICT's Advanced tech battles global cyber adversaries
DICT showcases advanced capabilities in response to attacks, highlighting the need for strategic cybersecurity measures at all levels
By Wilson Chua
At A Glance
- The Department of Information and Communications Technology (DICT) has demonstrated significant advancements in its cybersecurity capabilities, effectively acting as a deterrent to potential attackers. The ability of the DICT to not only monitor gov.ph online presence routinely but also to identify the groups behind these attacks showcases the department's sophisticated technological tools and the importance of having such capabilities to understand and mitigate evolving cyber threats.
- The attacks, while originating from China, present a complex challenge in directly implicating the Chinese state. The observation by Undersecretary Jeffrey Ian Dy that attacks often come from compromised servers rather than directly from the perpetrators themselves highlights the intricate nature of cyber warfare, where the geographical origins of attacks do not straightforwardly indicate the attacker's identity or affiliations.
- Recommendations for enhancing cybersecurity on a personal and organizational level include subscribing to Cyber Threat Intelligence, promptly patching systems, running antivirus checks, analyzing security logs daily, and fine-tuning firewall settings. These measures are essential for maintaining a proactive defense against the dynamic and evolving nature of cyber threats.
- At the national level, there's a push for legislative changes requiring Internet Service Providers (ISPs) to take more responsibility in responding to abuse reports.
- The discussion around ISPs' role in cybersecurity underscores the importance of collaboration and responsiveness to abuse reports. The correlation between ignored abuse emails and network vulnerability points to a larger issue of how cyber defenses can be compromised by inaction.
Newly released reports reveal cyberattacks on Philippine government networks, attributed to the LonelyIsland, Meander, and Panda groups. In reaction, under the leadership of Secretary Ivan Uy, the Department of Information and Communications Technology (DICT) has showcased its advanced cybersecurity capabilities and strategies to address these threats.
Here are some of the points that is worth noting:
1. DICT’s Display of Skills and Capabilities:
The DICT’s advanced cybersecurity capabilities acts as a powerful deterrent to would be attackers. Whereas in the past, cyber incursions were left unchallenged, today, the DICT enables each Gov.ph online presence to be routinely monitored. The DICT’s ability to identify not only the attacks but also the groups behind the attack is equally impressive.
Considering that the Emissary Panda group is a known stealth operator, identifying its incursion requires incredible skills and patience. This highlights the sophistication of DICT’s technologies, providing valuable insights into the evolving landscape of cyber threats.
2. Attribution to Chinese State?
Despite the attacks originating from China, it’s crucial to note that implicating the Chinese state is not so straightforward. Usec Dy rightly points this out. In addition, BNSHosting can cite parallels with other cases:
a. Just as PLDT is ranked 3rd as a major source of attacks, it does not mean that PLDT is the perpetrator itself. It only means that the attacks came from PLDT-owned IP addresses. In the same vein, China Unicom’s IP addresses ( №31, Jin-rong Street) that are the #1 source of the attacks may have been used as compromised servers as well.
Worldwide, the trend is hackers rarely launch attacks from their own country of origin:
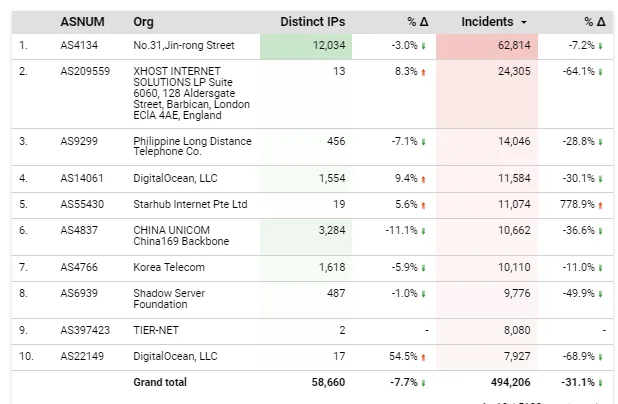
b. In fact, UK (2nd) and US (4th, 10th) are the OTHER major sources of cyber incursions. Again, we note that attackers often operate from servers outside their home country.
3. Protecting Yourself:
To enhance personal and organizational cybersecurity, consider the following measures:
a. Subscribe to Cyber Threat Intelligence:
Stay informed about evolving threats. These intel feeds often provide a list of IP addresses that are known to be cyber attackers. Blocking these IP addresses would stop any attacks from reaching your networks.
b. Patch Systems Promptly:
Should attacks breach your firewall, a regularly updated and patched system that reduces vulnerabilities will surely frustrate attackers and make their lives harder.
c. Run Anti-virus Checks:
Use reliable anti-virus software to scan for and remove malicious programs.
d. Analyze Security Logs Daily:
As cyber-attacks regularly change patterns, so must your network and security teams regularly review security logs to detect and respond to potential threats.
e. Fine-tune Firewall Logs Daily:
Optimize firewall settings to enhance network security by using the analytics from your security logs to fine-tune their settings.
4. National Level Solutions:
To bolster cybersecurity at a national level, consider:
a. Legislation for ISPs:
Mandate ISPs to respond promptly to abuse reports based on the severity of threats. Currently, ISPs can ignore any abuse emails that they get from the internet community. These abuse emails often warn them of potentially compromised servers inside the recipient’s network. By ignoring these alerts, the ISPs are allowing the infection/compromise to spread further inside their network. This makes matters even worse. (See Emissary Panda’s penchant for Watering hole attacks).
This writer is amazed at the correlation between undelivered “mail full” errors to abuse emails AND the vulnerability of these networks. The more abuse emails that remain ignored, the higher the likelihood that these networks are vulnerable to attacks.
b. Maintain a Common Cyber Threat Database:
It is just common sense to share cyber attack intelligence among PH networks. An attack on one raises the alarm for the rest of the PH network. I hope the Government can establish a downloadable cyber threat database, similar to existing lists for anti-gambling(NTC) or banking anti-scam (Globe), anti-porn/COPA (PLDT), to facilitate collective defense against cyber threats.
By staying vigilant and implementing these measures, both individuals and the nation can contribute to a more resilient cybersecurity landscape.