Distributed Denial-of-Service (DDoS) attacks have doubled in 5 years (2018 to 2023). It also evolved over time. We see hackers using Spoofed IP addresses while launching attacks from compromised servers. Hackers adopted this tactic of using spoofed IP addresses to “cover their tracks”. Changing the IP addresses makes it appear as though the attacks come from somewhere else. This makes it more difficult to trace and block the attacks.
The significance of this research becomes apparent when considering the harmful impacts on victims. These include a loss of trust, heightened susceptibility to further attacks, and increased complexity that hinders effective mitigation efforts — implementing robust countermeasures depend on accurately identifying the source IP. The ability to detect spoofed IPs has become an urgent necessity in safeguarding systems against evolving cyber threats.
A study is currently underway that explores how Machine Learning (ML) can be used to detect spoofed IP addresses. This can identify and classify source IP addresses as either legitimate (“Real”) or maliciously altered (“Spoofed”). Machine Learning offers a scalable, data-driven approach to tackle this issue by analyzing patterns and anomalies that traditional methods might miss. One choice of algorithm is the Random Forest Classification. Early results have been promising so far:
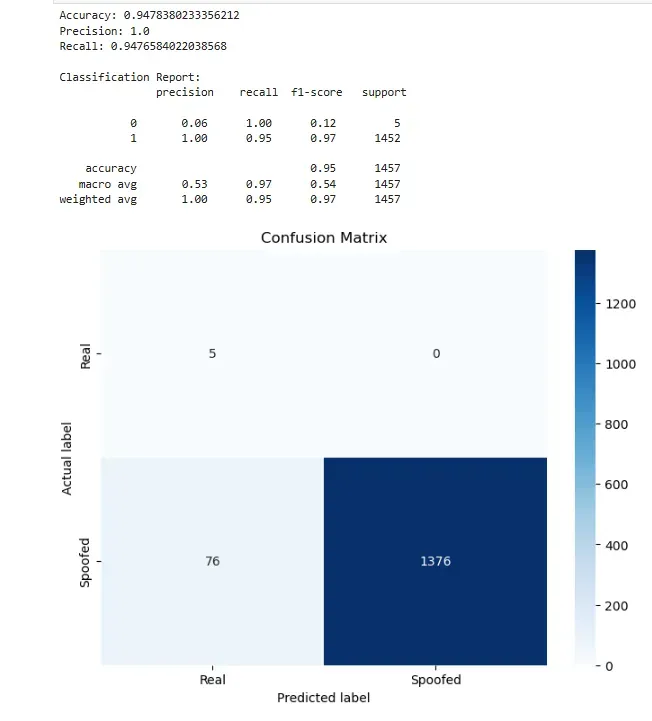
This robust method is also ‘explainable’ algorithm. Random forest provides the reader with the basis for the model. The research on Random Forest models for this purpose marks an important step forward in cybersecurity, equipping organizations with advanced tools to defend against ever-evolving threats in the digital landscape.